ChatGPT may be the AI on everyone’s mind right now, but chatbots aren’t the only AI tool we’ve seen recently. There are AI image generators like DALL•E 2, AI video generators such as Runway Gen 2 and more. Unfortunately, there are also AI password crackers — like PassGAN
Oddly enough, PassGAN isn’t all that new, at least relatively. It debuted back in 2017 (opens in new tab) and the most recent GitHub (opens in new tab) update was six years ago. In short, this isn’t some new hacking tool created in the wake of the ChatGPT revolution. However, cybersecurity research firm Home Security Heroes (opens in new tab) recently put it to the test and the results were alarming.
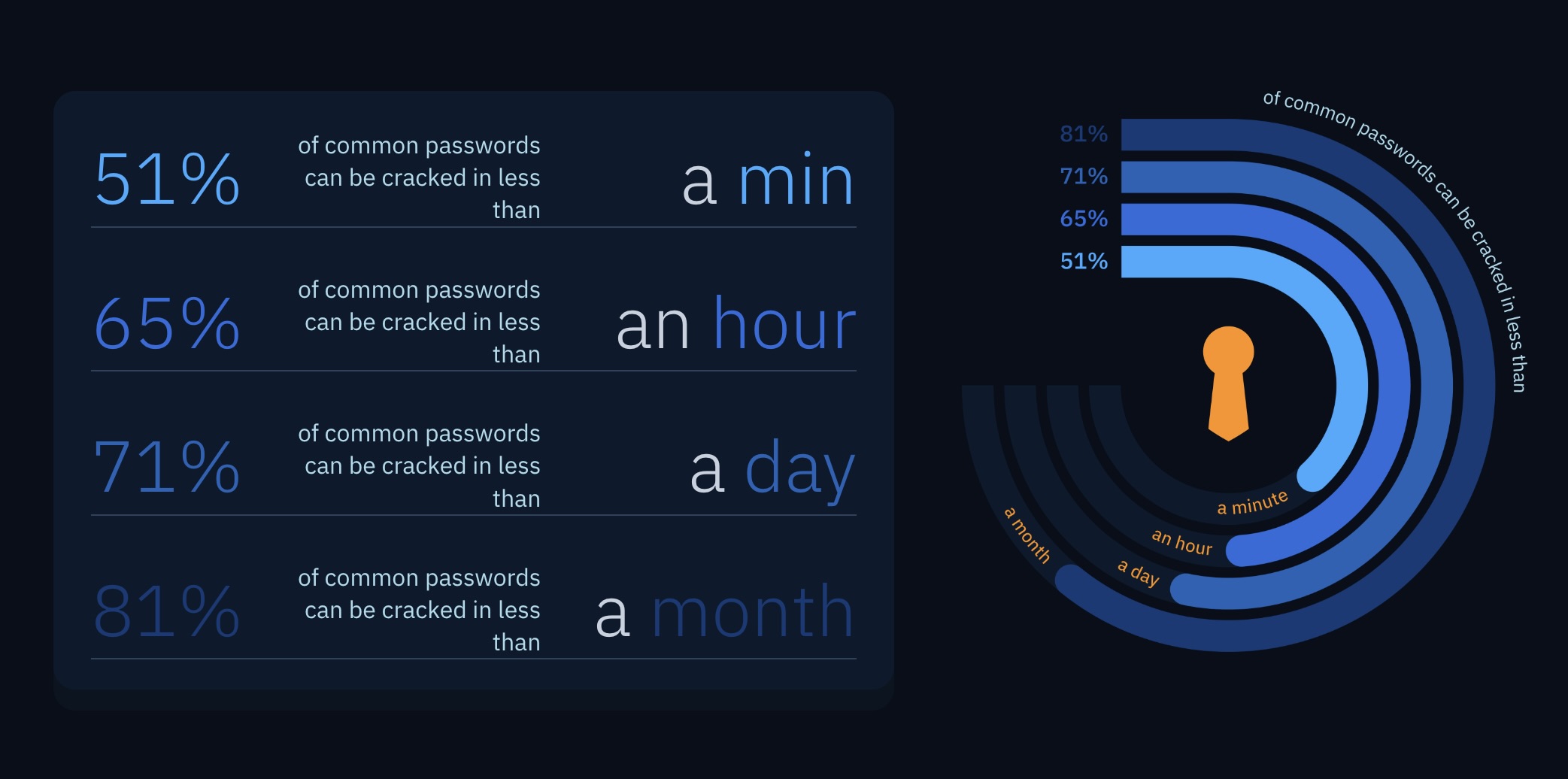
According to the Home Security Heroes study, PassGAN can crack any — yes, any — seven-character password in approximately six minutes or less. It doesn’t matter if it has symbols, uppercase letters or numbers, if it’s seven characters or less, PassGAN can crack it easily.
But before we get into how that affects you, and what you need to do, let’s quickly go over how PassGAN works.
How does PassGAN work?
PassGAN is a combination of Password and Generative Adversarial Network (GAN), much like how ChatGPT is a combination of Chat and Generative Pre-trained Transformer (GPT). GAN, like GPT, is essentially the deep learning model that the AI is trained on.
In this instance, the goal of the model is to generate password guesses based on real-world passwords that the model has been fed. For its study, Home Security Heroes used the RockYou dataset that arose from the 2009 RockYou data breach to train PassGAN, which is a widely used tool for studies such as these. The company fed PassGAN the data set and then got it to generate passwords in an attempt to correctly guess sample passwords. In the end, a wide variety of passwords were able to be cracked in mere seconds.
So after training PassGAN on the RockYou dataset, Home Security Heroes had an AI tool trained on real passwords that could now crack passwords instantly. But if it’s this simple, why shouldn’t everyone be panicking?
Do I need to panic over PassGAN?
The good news is that, no, you don’t really need to panic over PassGAN — at least not for now. In an op-ed, Ars Technica (opens in new tab) Security Editor Dan Goodin said that PassGAN was “mostly hype.” This is because while the AI tool can crack passwords with relative ease, it doesn’t crack them any faster than other non-AI password crackers.
In particular, Goodin cites Senior Principal Engineer at Yahoo Jeremi Gosney’s comments where he told Goodin that through conventional password-cracking tools, they could easily achieve similar results, cracking 80% of passwords similar to those in the RockYou breach within a few hours. For his part, Gosney said that the results from the Home Security Heroes study were “neither impressive nor exciting.”
And upon closer look at the results, you may find yourself less impressed than the initial claim of “50% of common passwords can be cracked in less than a minute.” These passwords are largely numbers only, seven characters or less, and rarely combine uppercase letters, lowercase letters, numbers and symbols.
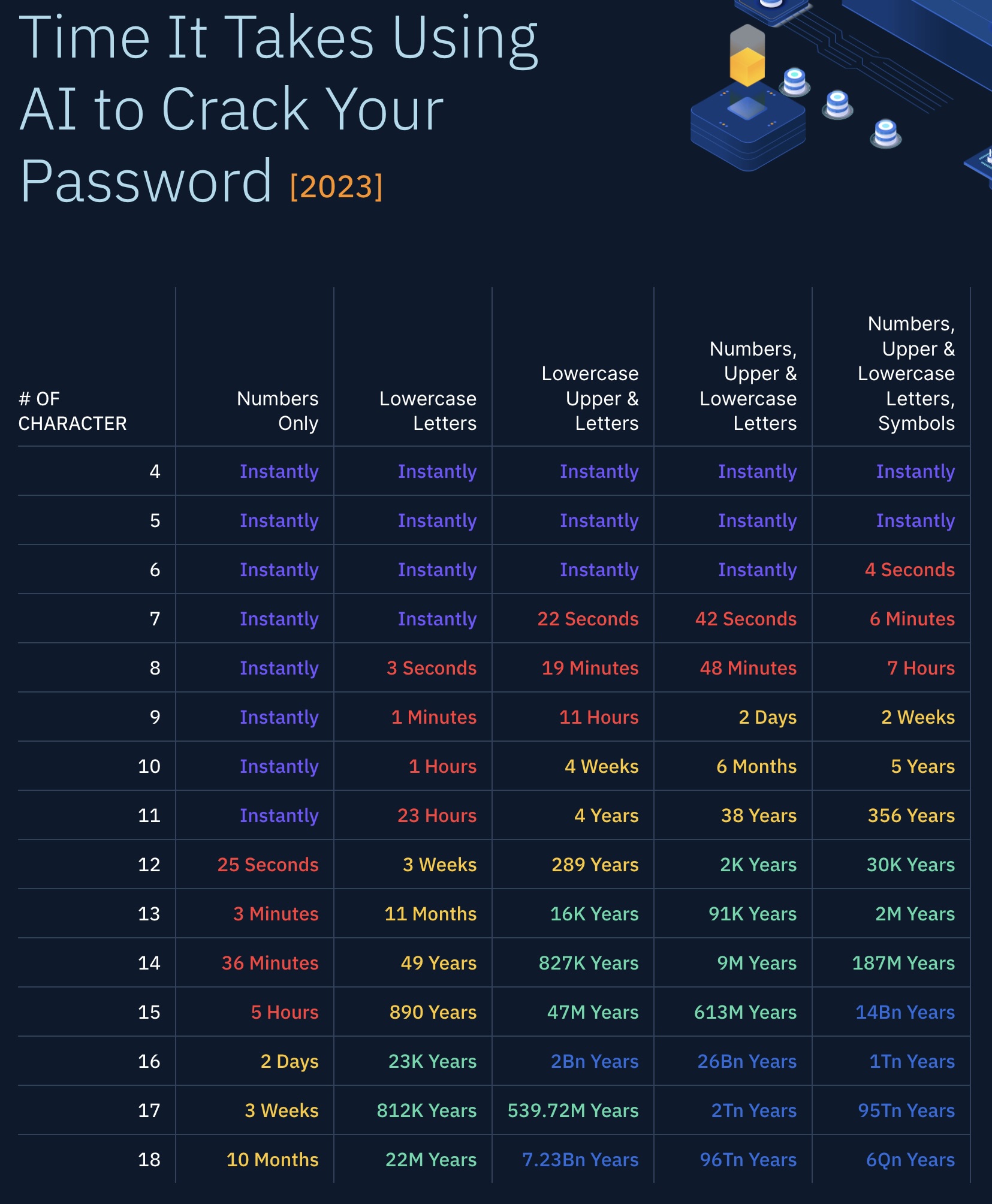
That means to stump PassGAN, all you need to do is create a password of 11 characters or more that includes a combination of uppercase and lowercase letters, numbers and symbols. If you manage that, you can create a password that will take PassGAN 365 years to crack. Increase that to 11 characters and that number becomes 30,000 years. And you can create these types of passwords easily with the best password managers.
But let’s say you don’t want to use a password manager because you don’t trust that they aren’t susceptible to data breaches — like the LastPass hack in August 2022. It’s not an unreasonable fear. Luckily, all you need to do is use a passphrase (multiple words combined to create a password) and you can still probably stump PassGAN. According to Home Security Heros, a 15-character password using just lowercase letters would still take PassGAN on average 890 years to solve. Add in just one capital letter, and that timeline could increase to a whopping 47 million years, long after our AI overloads have already conquered us.
Granted, no password is ever perfect. Data breaches can still leave you vulnerable despite your best efforts and a password cracker could get your password right earlier than expected through sheer dumb luck. But as long as you use the best practices for password security, you have nothing more to fear from PassGAN than any other bad actor.
